With the increasing use of digital systems on ships, cyber security has become extremely important. The maritime industry relies on these technologies for navigation, cargo management, communication, and other activities, which increases their vulnerability to cyber-attacks.
It is important for all stakeholders in the maritime sector to actively engage in enhancing cyber security practices. Cyber security measures should comply with international regulations and standards. For operational guidance, refer to the International Maritime Organization’s (IMO) webpage on cyber risk.
A cyber-attack on a vessel or maritime infrastructure could be devastating. Risks range from financial loss to potential loss of human life. Also, existing technologies (such as AIS or NAVTEX) do not include security measures. This makes them vulnerable to possible cyber-attacks.
Maritime Services should be “secure by design”. This means developers consider security in the design process and build it in from the start. (cf. IALA Recommendation 1024). Developers must ensure the confidentiality, integrity and availability of data at all times.
Authenticity of information
Ideally, all information we provide would be digitally signed. Recipients could check that the information came from us and that nobody had changed it. This applies to:
- navigational warnings issued by the JRCC
- information supplied by Vessel Traffic Services
- virtual and synthetic aids to navigation.
- Learn how digital signatures work
This scenario shows how we will use digital signatures to ensure the authenticity and integrity of our data.
- We issue a new navigational warning and sign it with our digital signature.
- We send the signed data to all vessels in NAVAREA X.
- Vessels receive the warning. They check the signature against a list of trusted entities in their onboard systems. If it matches, they know the warning came from us and they can trust the information it contains.
- The ECDIS displays the warning.
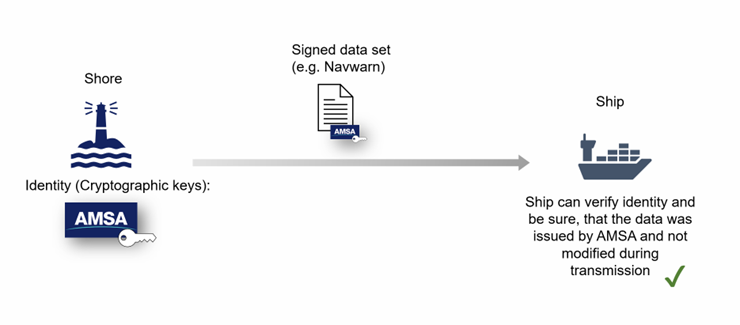
Using digital signatures to keep communications from AMSA secure
Confidentiality of information
Navigational warnings are public information and should be available to everyone. But there are other business processes that need the exchange of confidential information. For example, when vessels share cargo or crew data with public authorities.
You can encrypt data to protect its confidentiality using public key cryptography. Public key cryptography uses a pair of matching keys – one public and one private. When you encrypt data with a public key, only the holder of the matching private key can decrypt it.
- Learn how public key cryptography works
This example shows how an Australian port and an arriving vessel might exchange confidential FAL data.
- A vessel prepares its arrival in an Australian Port and wants to submit its digital FAL documents.
- The vessel obtains a public encryption key that is bound to the digital identity of the corresponding authority.
- The vessel uses this public key to encrypt the FAL documents.
- The vessel sends the encrypted data to the corresponding authority. Only the holder of the corresponding private key can decrypt the data.
- The corresponding authority uses its private key to decrypt the data. After decryption they process the FAL documents.
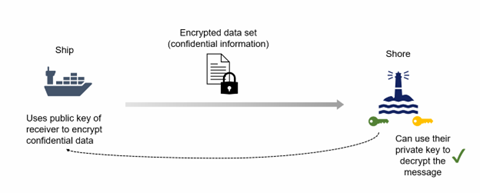
Using public key infrastructure to keep maritime communications confidential
The concept of private and public keys is a well-established technology. It is an essential feature of internet technology. We need new digital infrastructures to make maritime communications secure. Digital platforms such as the maritime connectivity platform can help.